OpenClaw AI Security Risks Every Business Must Know
OpenClaw exploded from obscurity to AI agent obsession practically overnight. What started as a coder's weekend project (opens in new tab) morphed into a must-have tool that enterprises chased for instant automation wins. But every shortcut carries a cost -within weeks, the real damage hit: data leaks, unauthorized code hitting live servers, and security teams scrambling through sleepless nights.
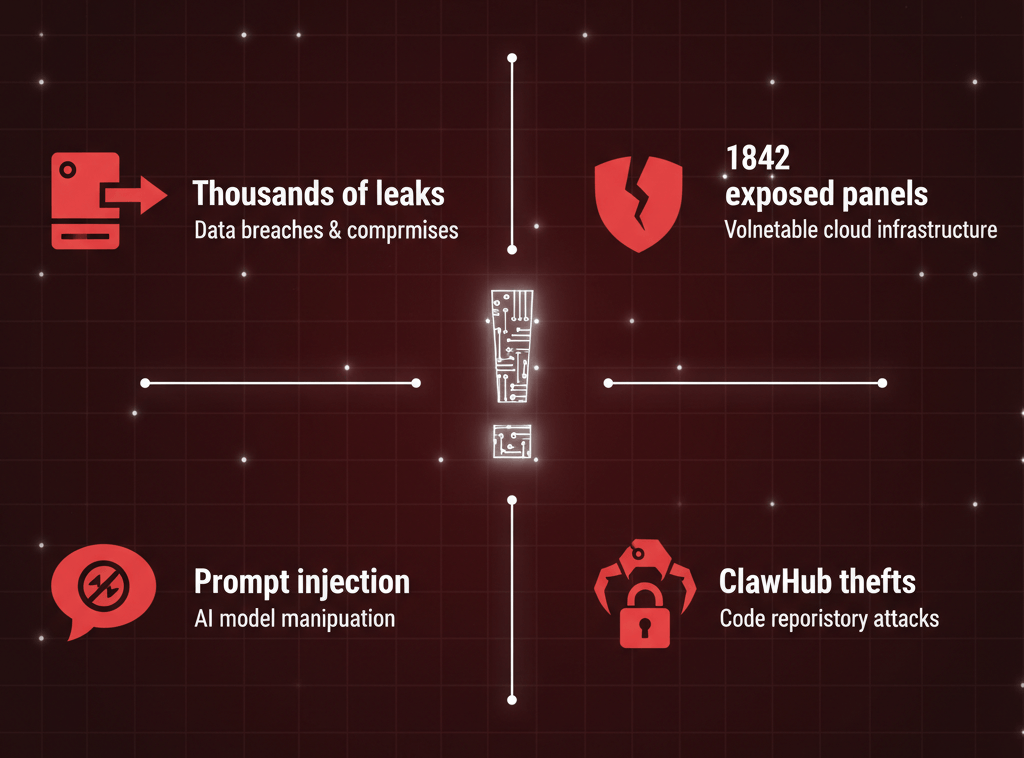
Researchers uncovered (opens in new tab) thousands of exposed OpenClaw instances leaking sensitive data, while Shodan scans (opens in new tab) revealed 1,842 control panels online - 62% with zero authentication.
Formerly known as Moltbot and Clawdbot (opens in new tab) during its rapid development phases, OpenClaw is an open-source AI agent framework that builds autonomous bots for sending emails, booking appointments, running code, and controlling systems through APIs. Its GitHub repo rocketed past 100,000 stars (opens in new tab) faster than React or TensorFlow milestones, outpacing enterprise rivals like LangChain agents or UiPath—businesses saw it as free firepower against pricey alternatives.
OpenClaw isn't just another chatbot. It dives (opens in new tab) deep into APIs, executes code, and automates workflows with minimal guardrails, amplifying risks as its enterprise blind spots widen. One wrong move exposes your data and hands attackers your systems. Latest patches plug bugs but leave the core flaws dangerously exposed.
Documented OpenClaw Security Fails
- Thousands of instances exposed data (opens in new tab) due to poor isolation.
- 1,842 control panels found online (opens in new tab), 62% unauthenticated.
- Prompt injection still tricks (opens in new tab) agents into leaking secrets.
- Malicious "skills" spread (opens in new tab) crypto stealers via ClawHub.
What's New: OpenClaw Growth and Latest Fixes
These vulnerabilities (opens in new tab) aren't unique to OpenClaw - prompt injection and weak sandboxing plague many early AI agent tools, from Auto-GPT to custom LLM agents. What sets OpenClaw apart is its scale: community-driven with no corporate backing, it lacks the compliance layers found in paid platforms. Patches like v2026.1.30 fixed specific RCE and LFI bugs, but adoption surveys show only 40% of users applied them within a month due to manual update requirements.
Adoption Timeline
OpenClaw's growth was meteoric. Within two weeks of wider exposure, its GitHub repository surged (opens in new tab) past 100,000 stars - faster than projects like React or TensorFlow took years to achieve.
OpenClaw's official GitHub page and demo site drew 2 million visitors (opens in new tab) in a single week per SimilarWeb analytics, as developers rushed to test it. Forum screenshots on Reddit's r/MachineLearning and Hacker News showed live automations handling emails and invoices, fueling enterprise interest.
For business owners, this felt like overnight disruption - forum screenshots showed live automations handling emails and invoices. OpenClaw has no corporate owner (opens in new tab); it's fully community-driven on GitHub with independent contributors. Being entirely free and open source fueled its viral spread among teams seeking quick AI wins.
Recent Patches
But rapid growth comes at a cost. Days after launch, researchers using AI pentester Hackian found a one-click RCE exploit (opens in new tab) - attackers could hijack OpenClaw via malicious WebSocket links, stealing gateway tokens and pivoting to local networks. This targeted how OpenClaw handled untrusted URL parameters in its default gateway interface.
A patch was committed on January 28 (commit 8cb0fa9) (opens in new tab) - just two days after discovery. Version v2026.1.30 later addressed (opens in new tab) related prompt injection gaps, where allowUnsafeExternalContent let attackers trick agents into executing shell commands or leaking API keys.
But users lagged behind. No auto-updates. No alerts. GitHub migration (opens in new tab) guidance from the original hosting platform was posted within hours on Discord, yet thousands of self-hosted deployments stayed vulnerable due to unclear upgrade steps.
Community Response
Trust cracked as security flaws outpaced fixes. OpenClaw maintainer Shadow warned on Discord: "If you can't understand how to run a command line, this is far too dangerous a project for you to use safely."
GitHub exploded with reports of prompt injection attacks (CVE-2026-22708) (opens in new tab) and plaintext API key leaks via unsecured endpoints (opens in new tab). Contributors demanded default sandboxing, but teams without dedicated security operations kept deploying default configs.
Bottom line: Patches chase vulnerabilities, but the core attack surface - gateway exploits, credential vaults, malicious skills - remains wide open. Businesses feel the heat as thousands of instances remain vulnerable.
Breaking Changes: Real Security Failures and Privacy Risks
Critical Vulnerabilities
For many teams, the OpenClaw launch felt like getting keys to a new sports car. Then, discovering the brakes hadn't been tested. The most alarming moment came January 26th, when AI pentester Hackian proved one-click RCE via WebSocket gateway (opens in new tab).
Attackers used malicious URL parameters to steal authentication tokens - no login barrier needed. The victim's browser became an attack proxy, pivoting straight to local networks. Cisco (opens in new tab) separately warned these agents run with unrestricted file access and command execution by design.
Shodan scans found (opens in new tab) 1,842 control panels exposed online, 62% completely unauthenticated. Thousands more leaked data through poor isolation. One wrong setup and your entire infrastructure's compromised.
Privacy Breaches
OpenClaw promised "personal AI" integrating with email inboxes, document stores, CRMs, and calendars. Instead, researchers (opens in new tab) found thousands of instances exposed online due to poor data isolation.
Cisco confirmed (opens in new tab) the core problem: agents store plaintext API keys locally - easily stolen by infostealers or extracted via prompt injection. With email access, one malicious message with hidden instructions forwards customer PII. One injected document command indexes private files publicly.
Default configs offered (opens in new tab) no protection. File systems, credential vaults, messaging apps stayed wide open. Agents accessed everything their rules allowed - no warnings triggered.
Breaches surfaced weeks later during routine audits, after sensitive data already spread across unsecured endpoints and public indexes.
Unpatched Gaps
The v2026.1.30 update shipped January 30th (opens in new tab), delivering critical fixes for LFI vulnerabilities (opens in new tab) in the media parser, WebSocket RCE (opens in new tab) (commit 8cb0fa9 from January 28), plus Telegram threading (opens in new tab) and shell completion improvements (opens in new tab). These patches addressed researcher findings quickly, but core architectural risks weren't rebuilt.
Key gaps persist:
- Default configs enable host execution: Sandboxing defaults to "off" for the main agent
sandbox.mode: "off"(opens in new tab), requiring manualsandbox.mode: "tight"(opens in new tab) configuration for isolation. Tools likeelevatedshell access stay opt-in but dangerously accessible without hardening. - Marketplace skills need vetting: ClawHub (opens in new tab) third-party plugins bypass automatic sandboxing - malicious ones have stolen crypto wallets (opens in new tab), demanding users audit every extension manually.
- Logging and detection lags: While per-agent model status improved visibility, comprehensive audit trails remain inconsistent, letting breaches evade notice for weeks.
Whether from its Moltbot/Clawdbot days or current OpenClaw branding, early adopters carry (opens in new tab) forward permissive defaults behind those Shodan-detected exposures (opens in new tab). Fully upgraded instances still inherit plugin risks and misconfigs from initial setups.
Safety demands (opens in new tab) manual work: Lock down permissions, enable sandboxing, vet all ClawHub skills, and audit configs line-by-line. Until secure defaults and marketplace audits ship, OpenClaw stays a wide attack surface for teams skipping these steps.
Safer AI Agents Start With Smarter Decisions
OpenClaw's meteoric rise became a security disaster (opens in new tab) in weeks. Thousands of instances leaked data. 1,842 control panels sat exposed online. Plaintext API keys waited for infostealers.
v2026.1.30 patches arrived January 30th. They fixed LFI vulnerabilities and Telegram bugs. But the architecture stayed dangerously permissive—admin defaults, no sandboxing, unvetted marketplace skills.
Smart businesses demand containment from day one. Isolated sandboxes. Zero-trust permissions. Audited integrations. Real-world attack simulations before deployment.
OpenClaw forces manual hardening most teams lack time or expertise to implement properly. One skipped config becomes the breach headline.
Choose enterprise AI with built-in security. OpenClaw demands 6-8 hours of manual hardening most teams lack. Enterprise platforms ship containment by default. January proved the cost of skipping that step.
Conclusion
OpenClaw delivers powerful automation, but only for those prepared for its true costs. Hype promises "30-minute setups" and magic AI agents - reality demands 6-8 hours of security hardening, thousands in monthly API fees, and deep Linux expertise.
Businesses chasing viral demos face prompt injection risks, exposed panels, and unsandboxed system access that turn experiments into breaches. Skip the beta promises for enterprise platforms with built-in security and compliance.
January 2026 proved the pattern: rapid hype without maturity creates disasters. Choose proven tools over perilous potential.

Justas Česnauskas
CEO | Founder
Builder of things that (almost) think for themselves
Connect on LinkedIn

